Exploits Database by Offensive Security
OVERVIEW
EXPLOIT-DB.COM RANKINGS
Date Range
Date Range
Date Range
EXPLOIT-DB.COM HISTORY
LENGTH OF LIFE
LINKS TO WEB SITE
Kimine Göre Adamımdır Kimine Görede Şerefsizin Önde Gideni , Kişiye Göre değişiyor ama . Hiç Kimseyi kendimden üstün veyahutta Düşük görmem. Wow, amazing blog layout! How long have you been blogging for? Websites .
Este el blog de Agux. Un lugar donde todos podremos aprender con todos. Lunes, 11 de mayo de 2015. Tomando posesión en Windows 8. Esta entrada es algo que seguro, seguro, la mayoría de vosotros conocéis. Precisamente se encuentra en la partición destinada a un recovery.
Monday, May 23, 2011. Sunday, May 22, 2011. GerixWiFiCracker is GUI for Aircrack-ng suite, is designed for pentesting in a realworld with efficent and userfriendly graphic interface. Usually Gerix Wifi Cracker can be found in any backtrack version ,gerix quit fun easy to use . In next section i will show the demo about gerix. Thursday, April 7, 2011. To do the penetration testing it .
8230; aus dem Leben eines Sysadmins. Review of Open-E DSS v7. Initially, we were looking for a 10GE- iSCSI. Storage solution that would do synchronous or at least memory-synchronous mirroring. Of data to a second system and automatic failover. We planned to use the system as storage backend for a few dozens VMs. And wanted the storage to be highly available. Active-Active supported seemed pretty awesome too, and the system should allow seamless failover.
Posted in Firewall Blocked IPs. Posted in Firewall Blocked IPs. Posted in Firewall Blocked IPs.
Discussing development and coding of any type. In this post I will demonstrate how to take. Using Pound Reverse Proxy with Apache. When dealing with a high traffic web site it is often nice to implement some sort of caching mechanism or load balancer into your site architecture.
Memenuhi segala informasi tentang wisata ke Bali, paket liburan murah ke Bali, Hotel murah di Bali, Tour murah di Bali, Sewa kendaraan, kegiatan petualangan, dan lain-lainnya. Seorang pria dan kekasihnya menikah dan acaranya pernikahannya sungguh megah. Semua teman teman dan keluarga mereka hadir menyaksikan dan menikmati hari yang berbahagia tersebut. Suatu acara yang luar biasa dan mengesankan.
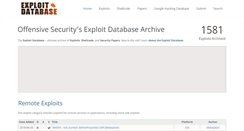
WHAT DOES EXPLOIT-DB.COM LOOK LIKE?
CONTACTS
Registration Privacy, No-IP.com
ATTN: exploit-db.com, c/o No-IP.com Registration Privacy
P.O. Box 19083
Reno, NV, 89511
US
EXPLOIT-DB.COM HOST
NAME SERVERS
WEBSITE IMAGE

SERVER OS
I observed that this website is employing the Sucuri/Cloudproxy server.PAGE TITLE
Exploits Database by Offensive SecurityDESCRIPTION
The Exploit Database - Exploits, Shellcode, 0days, Remote Exploits, Local Exploits, Web Apps, Vulnerability Reports, Security Articles, Tutorials and more.CONTENT
This domain exploit-db.com states the following, "Local Privilege Escalation Exploits." We observed that the website also said " Denial of Service PoC Exploits." It also stated " About The Google Hacking Database. Offensive Securitys Exploit Database Archive. 8211; ultimate archive of Exploits. New to the site? Learn about the Exploit Database. Download the Exploit Database Archive. Visit the Google Hacking Database. This exploit category includes exploits for remote services or applications, including client side exploits. In our labs, when possibl." The header had exploits as the highest ranking keyword. It was followed by shellcode, security papers, and exploit tutorials which isn't as ranked as highly as exploits. The next words the site used was Windows exploits. Linux exploits was also included but will not be viewed by search parsers.SEEK OTHER DOMAINS
com provides a variety of virtual machines, documentation and challenges that can be used to learn about a variety of computer security issues such as privilege escalation, vulnerability analysis, exploit development, debugging, reverse engineering, and general cyber security issues. Nebula covers a variety of simple and intermediate challenges that cover Linux privilege escalation, common scripting language issues, and file system race conditions.
Ce blog vous presente mes Exploit dans le serveur helsephine. Flash special est très important je stop. A bientot pour continuer a suivre mes aventure et celle de mon amis Choco. Lien du nouveau Blog - New blog. Actuellement 200, est dan.
Security Research and Esoteric PowerShell Knowledge. Tuesday, August 29, 2017. Exploiting PowerShell Code Injection Vulnerabilities to Bypass Constrained Language Mode. Is an extremely effective method of preventing arbitrary unsigned code execution in PowerShell. Add-Type is passed a global variable as its t.